As our economy continues to become more digital, the need to protect payment card data has never been greater. The Payment Card Industry Security Standards Council’s (PCI SSC) Data Security Standard (DSS) sets forth a collection of best practice security requirements to help merchants and service providers adequately secure their cardholder data environments (CDE). But achieving PCI compliance can be a daunting task for first-time compliers. Fortunately, the PCI Council recognizes the burden that first-time DSS compliance places on many organizations and has therefore published a helpful tool called the PCI DSS Prioritized Approach for PCI DSS 3.2.1 (Prioritized Approach or Approach) to outline and prioritize the actions organizations need to take to address their highest exposure (risk) areas earlier in the compliance process, and to eventually achieve full compliance. Using the Prioritized Approach will assist you in breaking down a large compliance effort into manageable and risk-prioritized milestones.
About the PCI DSS Prioritized Approach for PCI DSS 3.2.1.
The Prioritized Approach offers a pragmatic methodology that identifies highest risk targets, creates a common language around PCI DSS implementation progress reporting, provides consistency among assessors, and promotes incremental objectives and measurable progress. The Approach breaks down the DSS’s 12 requirements and 300+ sub-requirements into six logical and security-focused milestones and goals to help protect against the highest risk factors and security threats that stem from storing, processing, and transmitting cardholder data. The milestones (see chart below) are organized by risk, with the first one accounting for the highest security risk factors. The six milestones serve as markers to track progress in the compliance process.
PCI DSS 3.2.1. Milestones
Goals | Milestone |
1 | Remove sensitive authentication data and limit data retention. This milestone targets a key area of risk for entities that have been compromised. Remember – if sensitive authentication data and other cardholder data are not stored, the effects of a compromise will be greatly reduced. If you don’t need it, don’t store it |
2 | Protect systems and networks, and be prepared to respond to a system breach. This milestone targets controls for points of access to most compromises, and the processes for responding. |
3 | Secure payment card applications. This milestone targets controls for applications, application processes, and application servers. Weaknesses in these areas offer easy prey for compromising systems and obtaining access to cardholder data. |
4 | Monitor and control access to your systems. Controls for this milestone allow you to detect the who, what, when, and how concerning who is accessing your network and cardholder data environment. |
5 | Protect stored cardholder data. For those organizations that have analyzed their business processes and determined that they must store Primary Account Numbers, Milestone Five targets key protection mechanisms for that stored data. |
6 | Finalize remaining compliance efforts, and ensure all controls are in place. The intent of Milestone Six is to complete PCI DSS requirements, and to finalize all remaining related policies, procedures, and processes needed to protect the cardholder data environment. |
Source for above and below images: Prioritized-Approach-Tool-v3-2-1
Excel Tool
Also included in the Approach is a comprehensive Excel-based tool (see example below) that can be populated by the merchant, service provider, or QSA to help gauge and track the organization’s overall compliance status. The organization answers “Yes”, “No”, or “N/A” to each sub-requirement under the 12 main requirements. Once completed, you’ll receive a score from 0-100%, representing your overall compliance with the DSS.
Milestone | Goals | Percent Complete | Estimated Date for Completion of Milestone |
1 | Remove sensitive authentication data and limit data retention. This milestone targets a key area of risk for entities that have been compromised. Remember – if sensitive authentication data and other cardholder data are not stored, the effects of a compromise will be greatly reduced. If you don’t need it, don’t store it | 100.0% |
|
2 | Protect systems and networks, and be prepared to respond to a system breach. This milestone targets controls for points of access to most compromises, and the processes for responding. | 74.4% | February 29, 2020 |
3 | Secure payment card applications. This milestone targets controls for applications, application processes, and application servers. Weaknesses in these areas offer easy prey for compromising systems and obtaining access to cardholder data. | 65.9% | February 29, 2020 |
4 | Monitor and control access to your systems. Controls for this milestone allow you to detect the who, what, when, and how concerning who is accessing your network and cardholder data environment. | 66.6% | March 31, 2020 |
5 | Protect stored cardholder data. For those organizations that have analyzed their business processes and determined that they must store Primary Account Numbers, Milestone Five targets key protection mechanisms for that stored data. | 90.0% | March 31, 2020 |
6 | Finalize remaining compliance efforts, and ensure all controls are in place. The intent of Milestone Six is to complete PCI DSS requirements, and to finalize all remaining related policies, procedures, and processes needed to protect the cardholder data environment. | 54.1% | March 31, 2020 |
Overall | 70.0% | March 31, 2020 |
By populating the spreadsheet with estimated task completion dates, organizations can keep their compliance efforts on track. Regular updates, such as changing a “NO” to a “YES” when milestones are reached, will automatically change the overall score to reflect the efforts towards total compliance. This score can easily be shared with stakeholders as a measure of compliance progress.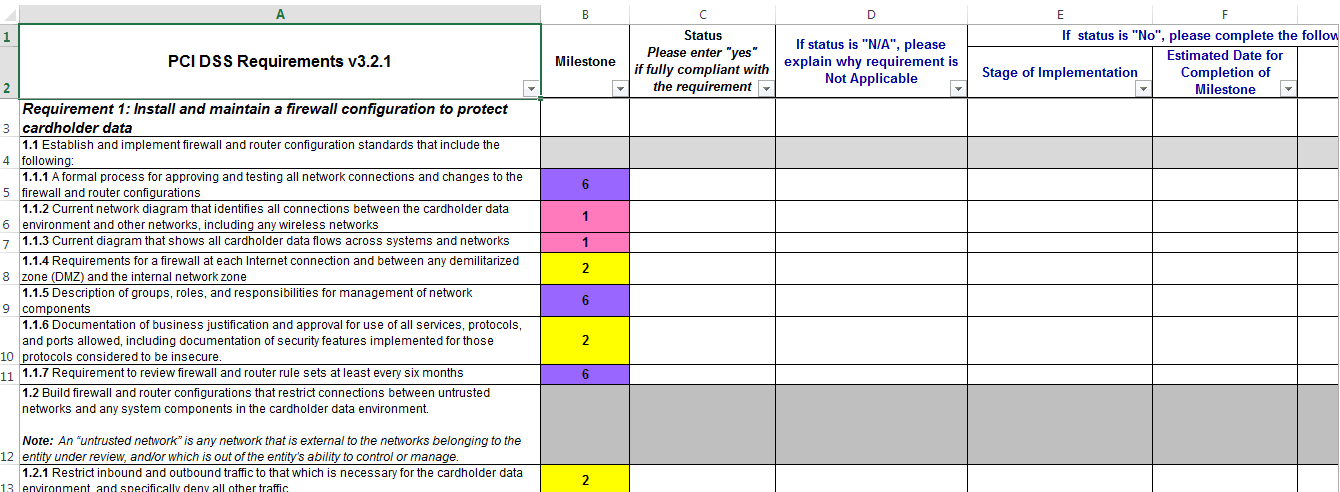 Obtaining PCI DSS compliance is necessary for organizations participating in the card payment process. The PCI Security Standards Council’s Prioritized Approach offers stakeholders a comprehensive measuring stick for their compliance status and helps them prioritize their efforts in a risk-based manner.
Obtaining PCI DSS compliance is necessary for organizations participating in the card payment process. The PCI Security Standards Council’s Prioritized Approach offers stakeholders a comprehensive measuring stick for their compliance status and helps them prioritize their efforts in a risk-based manner.
About the Author

Mindy Milliet is a certified PCI Qualified Security Assessor with over 18 years of experience in internal audit, IT audit, and data security. With her extensive SOX, internal audit and security audit experience, Mindy works with clients across a wide range of industries with a focus on financial services, restaurants, hospitality, manufacturing, distribution, healthcare and traditional and eCommerce retail.
